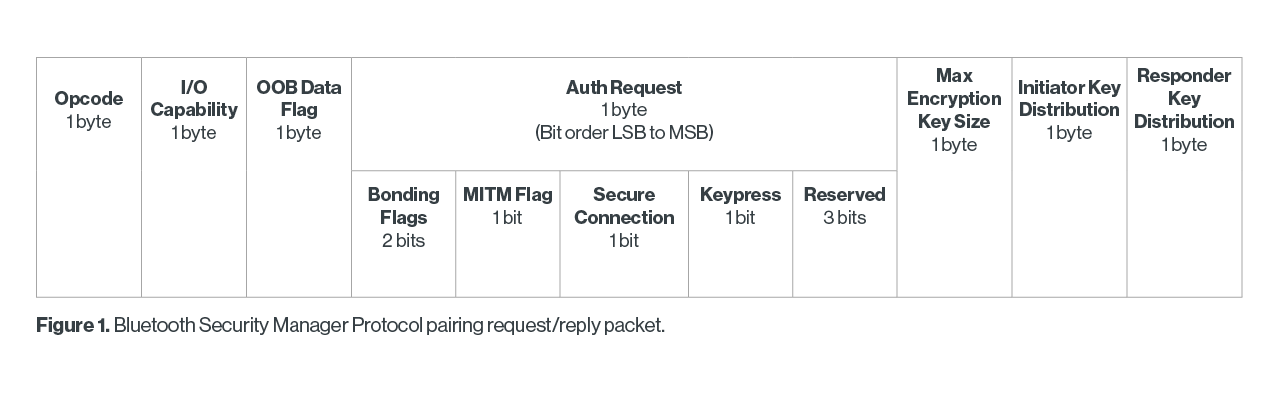
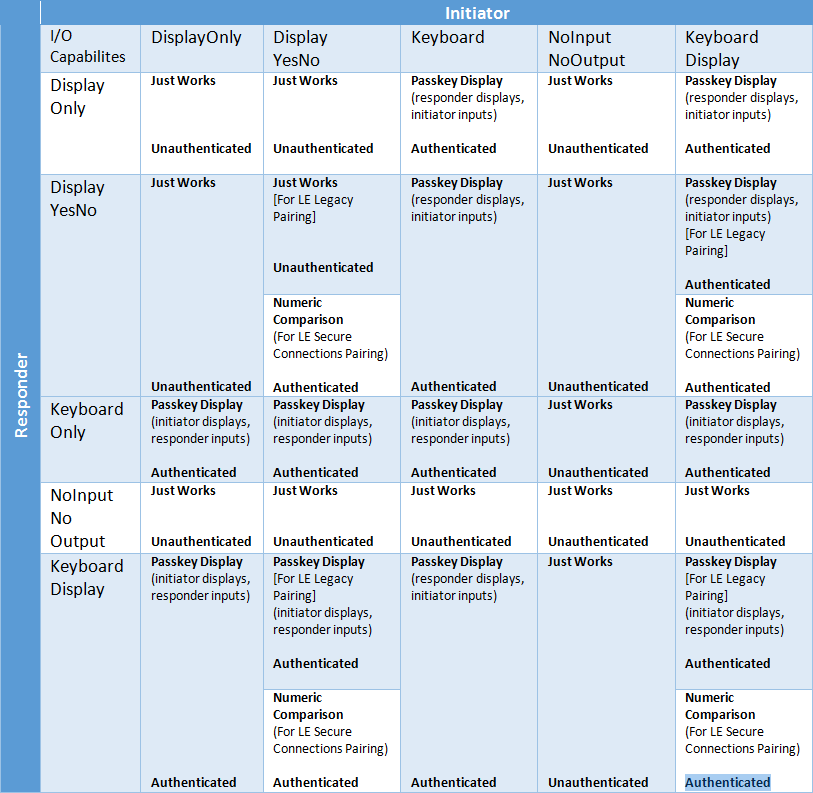
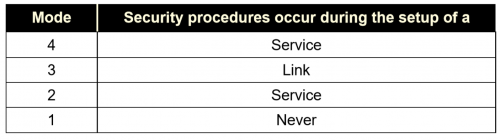
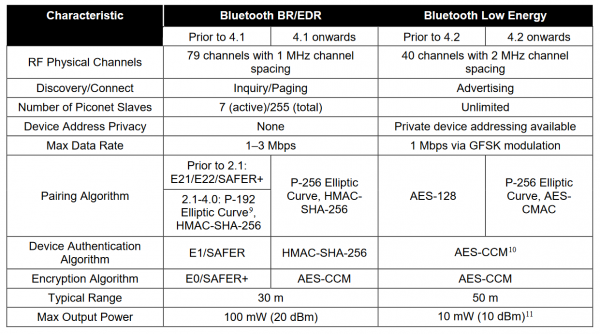
Project Proposal: Security Threats for Wireless Devices Matt Fratkin April 11 th, 2005 E ppt download

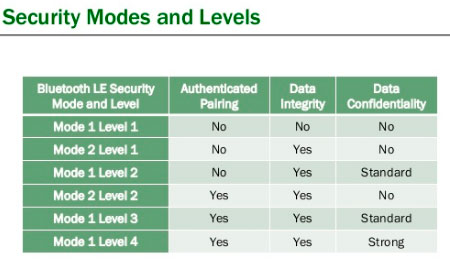
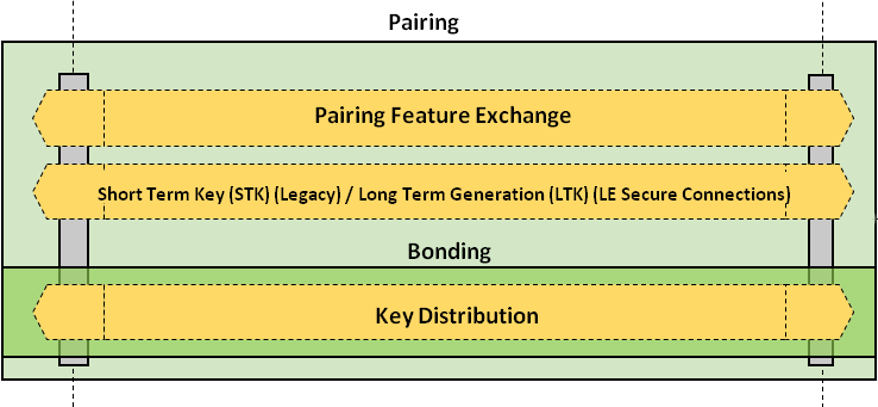
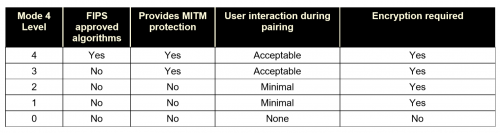
1: Overview of the Bluetooth Key Generation Routines for Security Modes... | Download Scientific Diagram

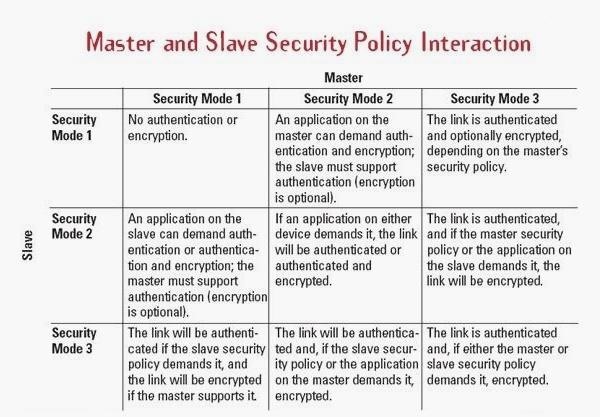
Block Diagram of Bluetooth Encryption The Bluetooth has three different... | Download Scientific Diagram