DIY Information Security Program: It Takes the Full Village to Effectively Steward Our Data - The Tambellini Group
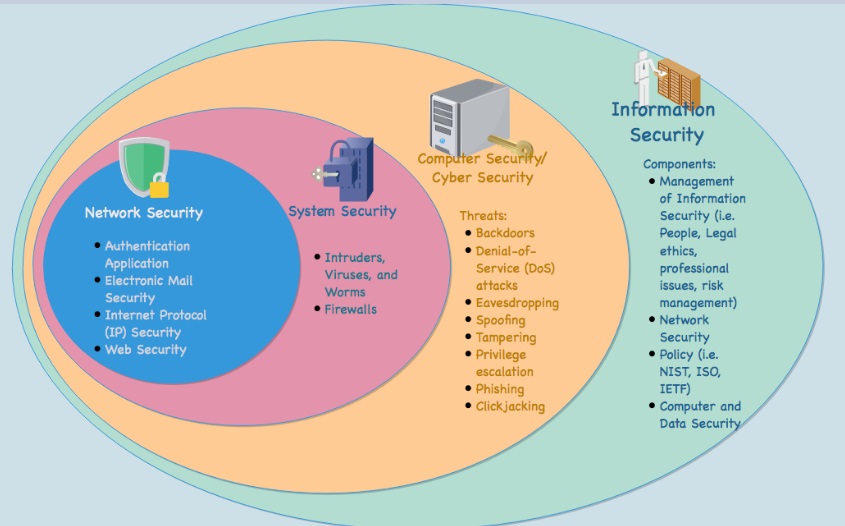
What's the Difference Between Information Security and Cyber Security? | Cyber Security Career Advice

Cyber Security, Protection of Information Data. the Concept of Data Protection. Stock Illustration - Illustration of isolated, network: 116535543
















![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/10/Three-pillars-of-information-security-and-cybersecurity.png)