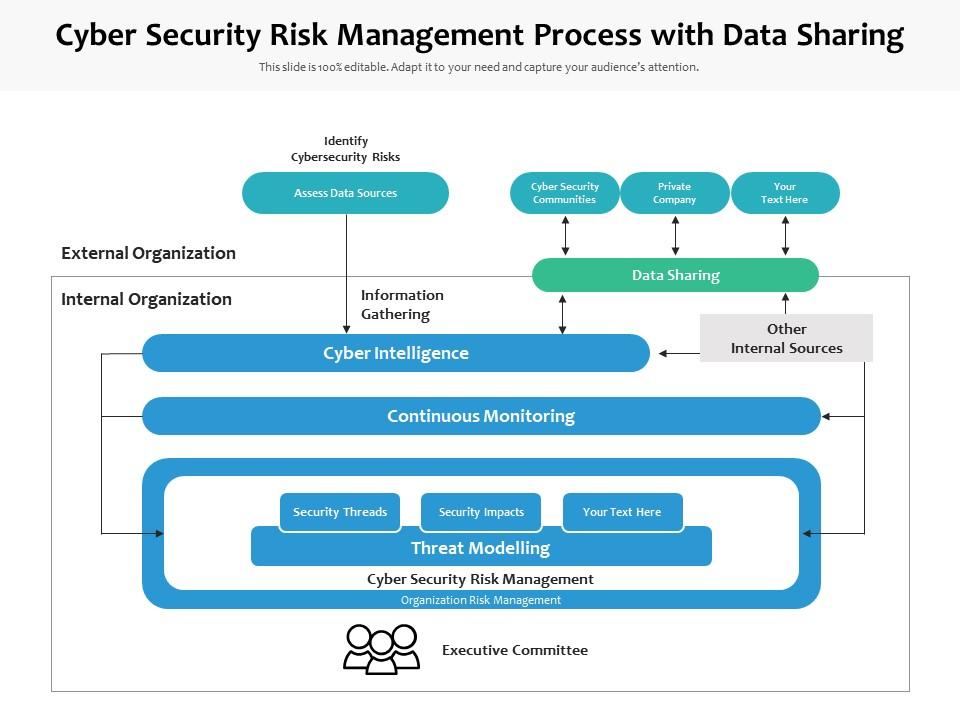
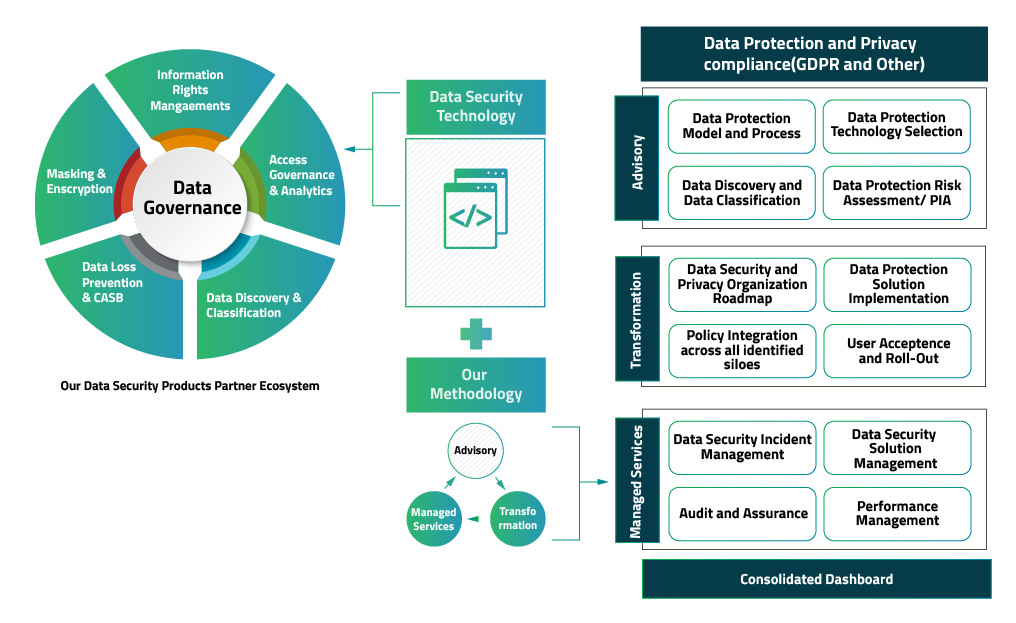
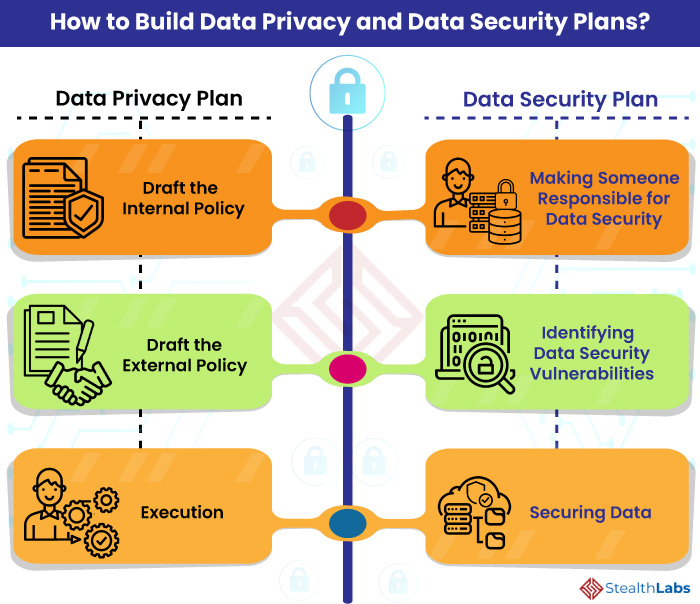
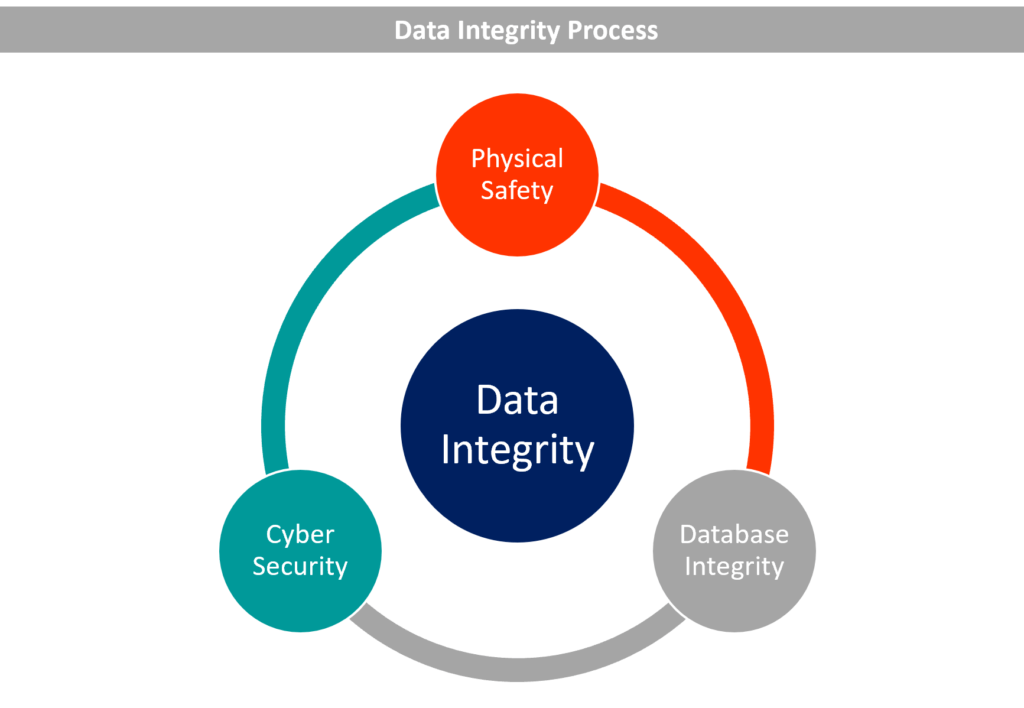
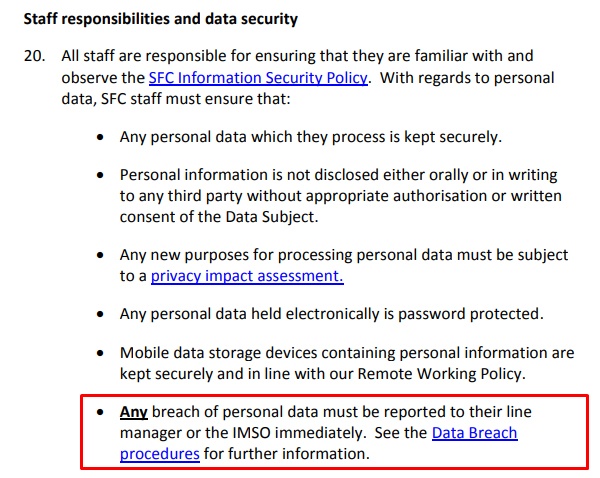
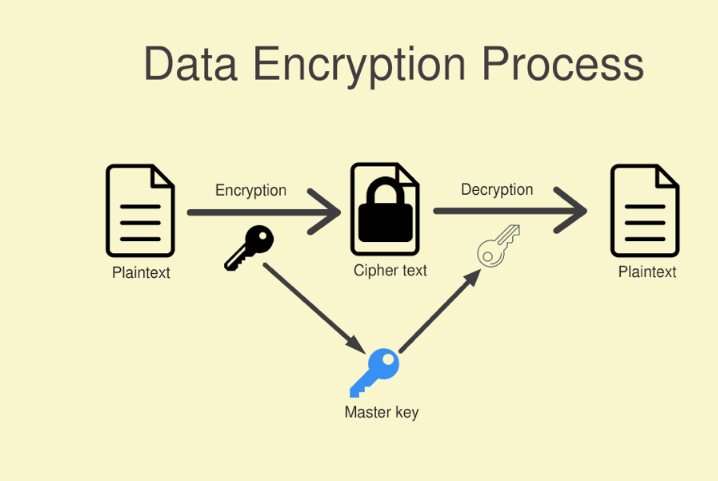
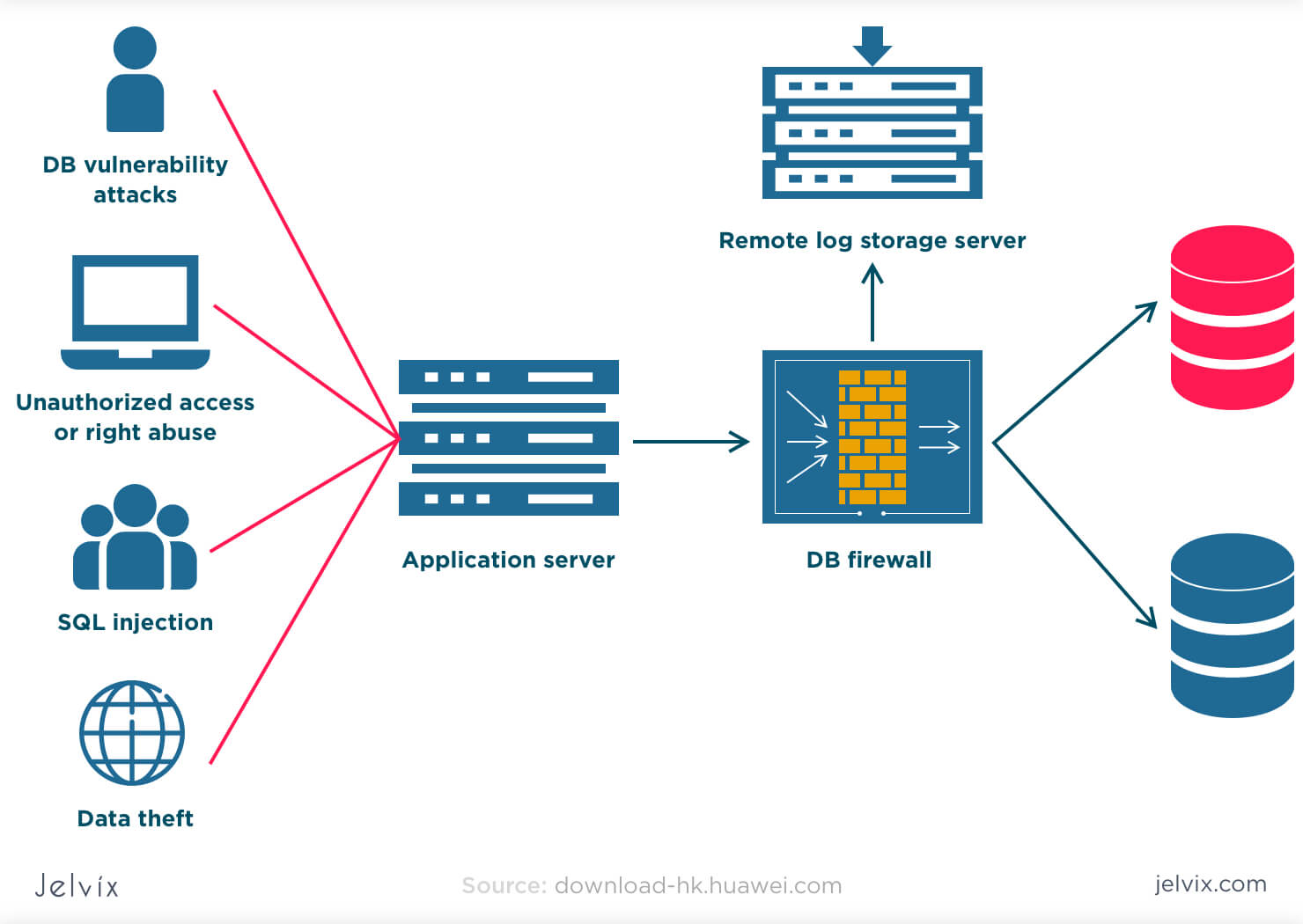
8 IT Security Processes to Protect and Manage Company Data | Process Street | Checklist, Workflow and SOP Software

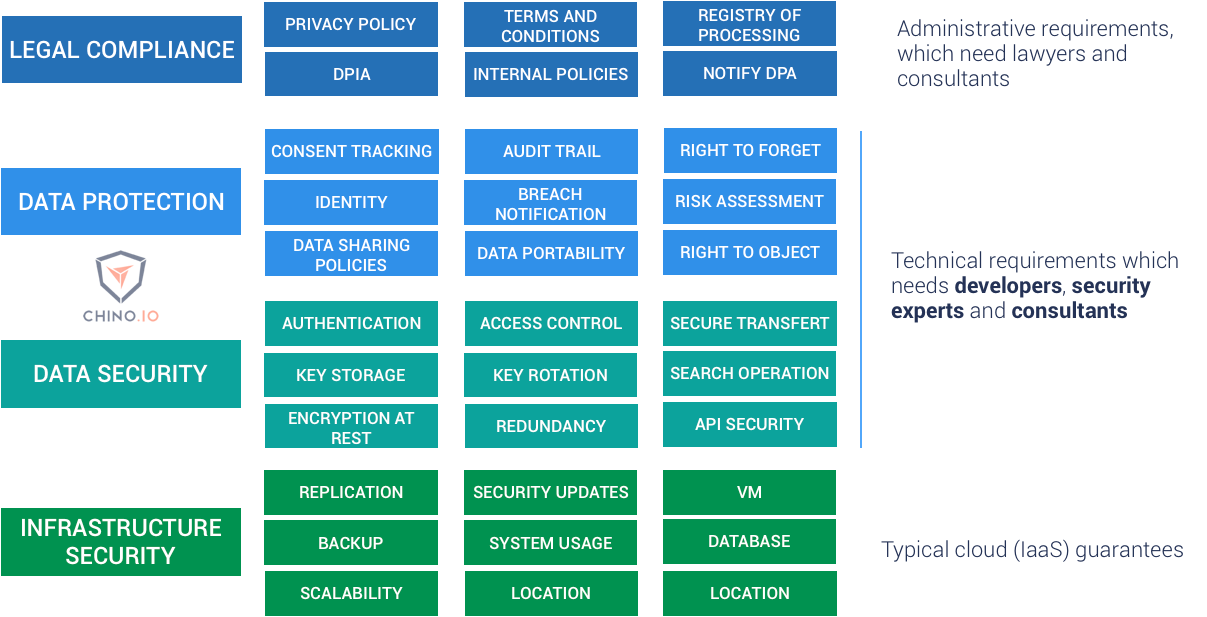
Best Data Security Software Process Flow For Company Online Database Security Elements PDF - PowerPoint Templates

D14.2: Study on Privacy in Business Processes by Identity Management: Future of IDentity in the Information Society