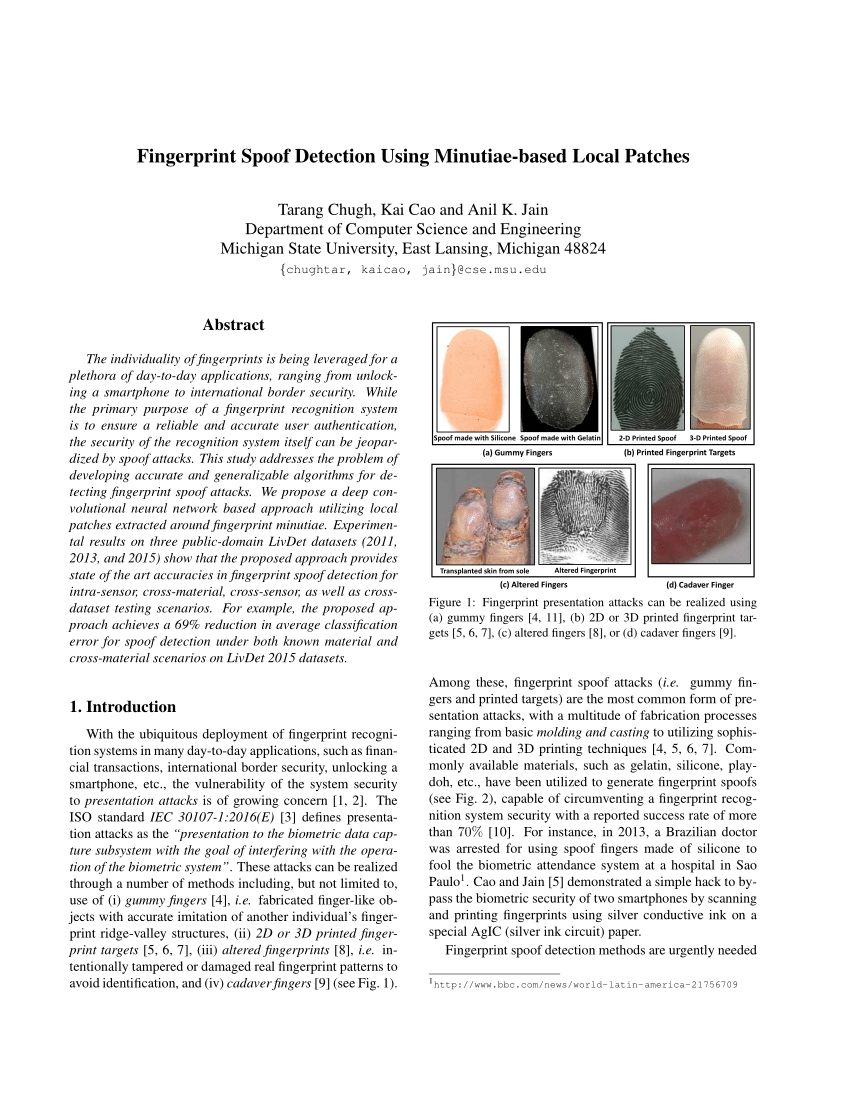
Example fingerprint images from live (top), spoof (middle), and cadaver... | Download Scientific Diagram

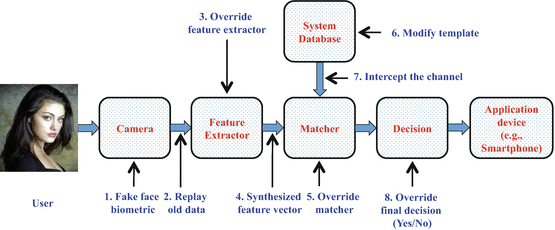
Fingerprint Spoofing Detection to Improve Customer Security in Mobile Financial Applications Using Deep Learning | SpringerLink

Fingerprint Spoofing Detection to Improve Customer Security in Mobile Financial Applications Using Deep Learning | SpringerLink

Anti-spoofing method for fingerprint recognition using patch based deep learning machine - ScienceDirect
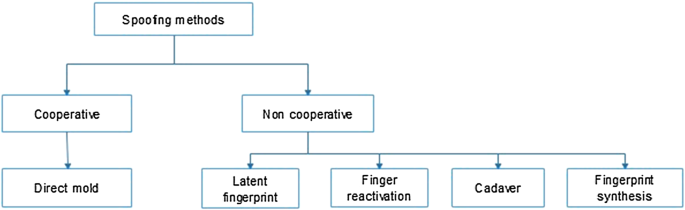
Fingerprint Spoofing Detection to Improve Customer Security in Mobile Financial Applications Using Deep Learning | SpringerLink

Anti-spoofing method for fingerprint recognition using patch based deep learning machine - ScienceDirect
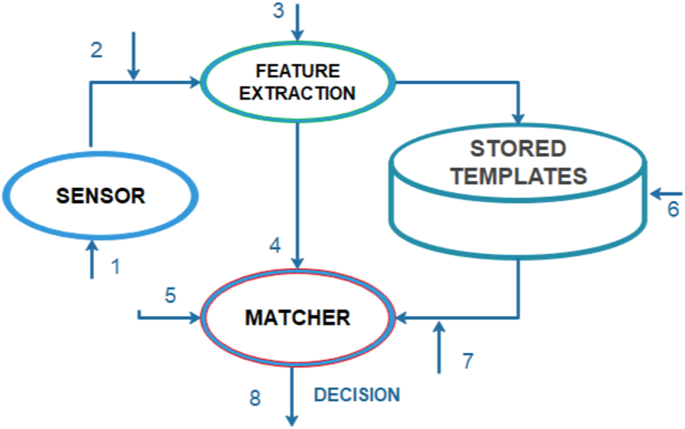
Fingerprint Spoofing Detection to Improve Customer Security in Mobile Financial Applications Using Deep Learning | SpringerLink