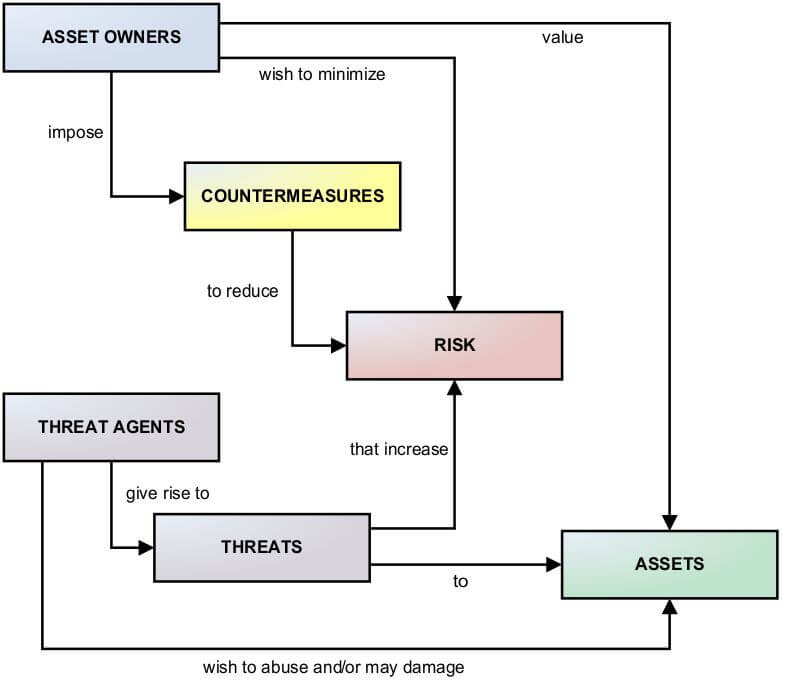
Dentons - China's GDPR is Coming: Are You Ready? Exploring the Upcoming China's Draft Personal Information Protection Law Topic Ten – Cross-border Transfer of Personal Information

Cyber Security Law Digital Legislation 3d Illustration Stock Illustration - Illustration of guard, safe: 126890128

Beyond the Worst-Case Assumptions on China's Cybersecurity Law | Center for Strategic and International Studies