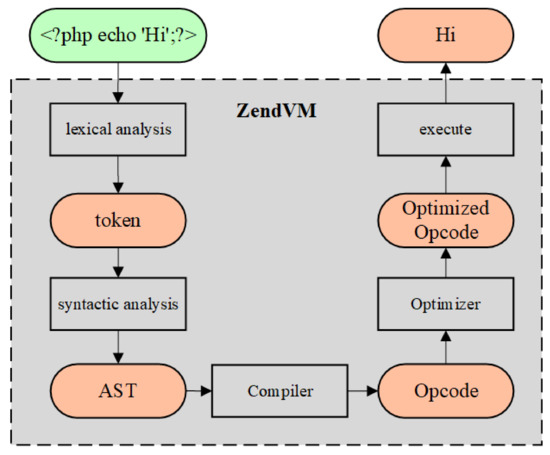
Eric Bodden on Twitter: "All three badges for our #FSE18 reproducibility study on Android taint analysis tools! Yeah! https://t.co/UUssCuXbbm" / Twitter

USING TAINT ANALYSIS TO TRACE WHETHER THE MODULE IS CONTAMINATED VIA... | Download Scientific Diagram
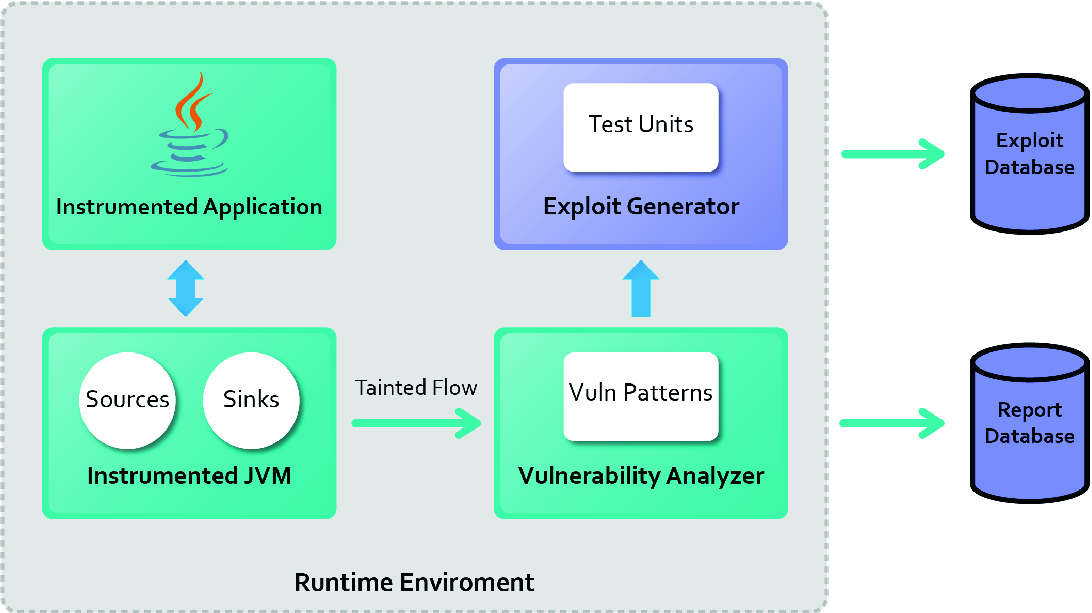
Practical Dynamic Taint Tracking for Exploiting Input Sanitization Error in Java Applications | SpringerLink

MOV instruction is instrumented for dynamic taint analysis. The first... | Download Scientific Diagram

COVA: A Static Analysis Tool for Computing Partial Path Conditions | by Linghui Luo | ASE Conference | Medium

Use of taint analysis to determine whether the module is contaminated... | Download Scientific Diagram

Static program analysis assisted dynamic taint tracking for software vulnerability discovery - ScienceDirect

![equation]: Backward Context-Sensitive Flow Reconstruction of Taint Analysis Results | SpringerLink equation]: Backward Context-Sensitive Flow Reconstruction of Taint Analysis Results | SpringerLink](https://media.springernature.com/original/springer-static/image/chp%3A10.1007%2F978-3-030-39322-9_2/MediaObjects/487236_1_En_2_Fig2_HTML.png)


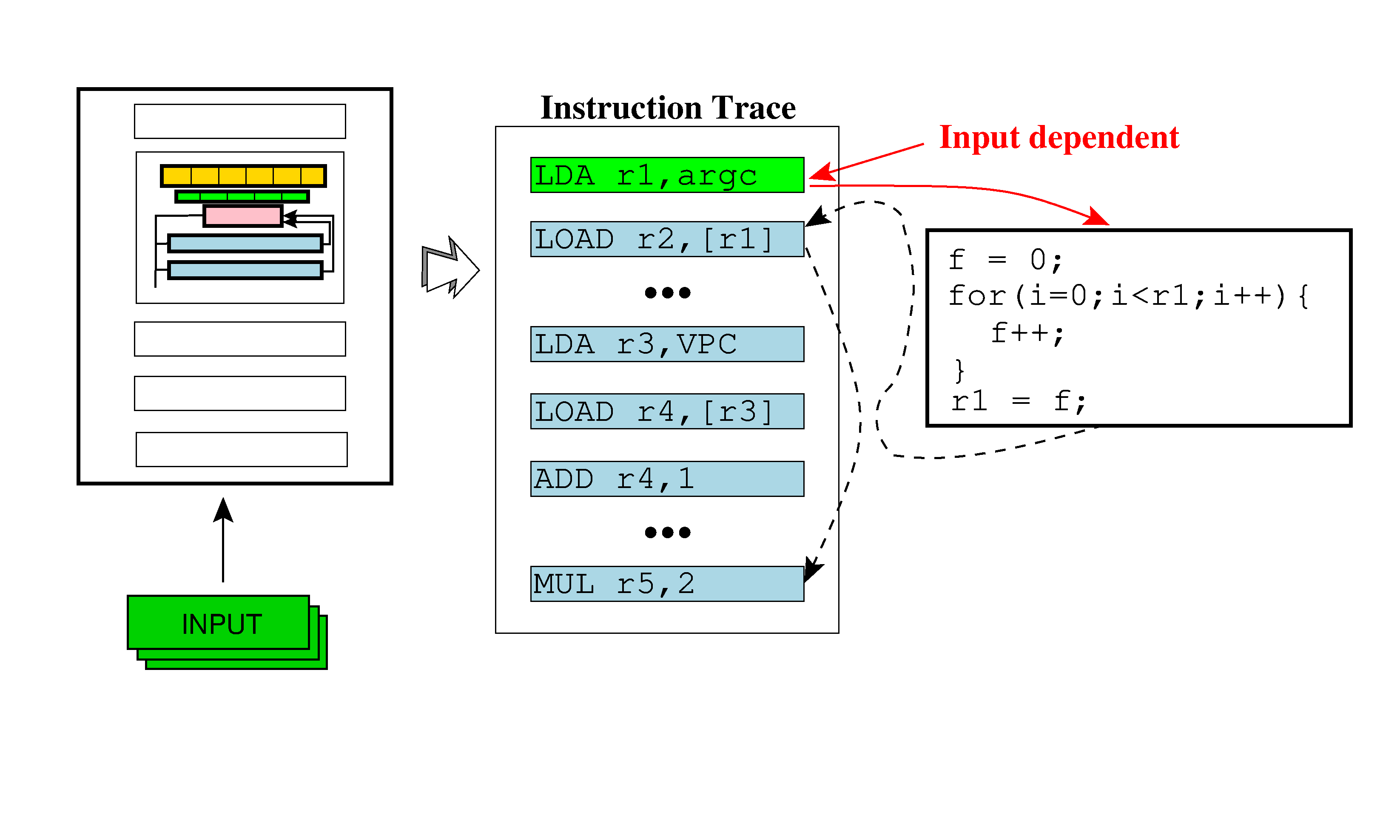

![PDF] Neutaint: Efficient Dynamic Taint Analysis with Neural Networks | Semantic Scholar PDF] Neutaint: Efficient Dynamic Taint Analysis with Neural Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/290142398d893cd3da83f821463478bf9f309a71/3-Figure1-1.png)